Can you trust Secure Shell (SSH) when you are behind certain firewalls? That’s the question raised by a post from a friend of mine:
It seems that because ssh can be used for tunneling services and application traffic several firewall vendors are now implementing “SSH inspection” services that essentially perform a Man-in-The-Middle (MITM) attack on your ssh connection.
When you go to ssh into a server, the firewall pretends it is that server and creates a ssh tunnel with you. The firewall then creates the actual ssh connection to the server and passes your packets from the first tunnel into the second tunnel – while being able to log or inspect the packets in between the two tunnels.
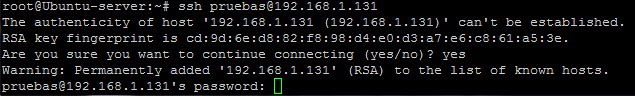
Now, of course with ssh you go through an initial handshake when you first connect to a server that results in the server’s public key being added to your list of known hosts.
If you connect to a server for the first time BEFORE being behind one of these firewalls doing SSH inspection, you would already have the correct public key of the server in your known hosts file. What would happen when the firewall tried to do a MITM is that you would be asked to approve the public key of the server again. (Because you are actually now approving the public key of the firewall.)
You would have to realize that this was wrong and stop your connection!
If you proceeded ahead with the connection and approving the public key, you would now have the firewall as a MITM.
If you connect to a server for the first time AFTER being behind one of these firewalls, well… I’m not sure what you can do. You’re going to see a public key to approve, but it would be from the firewall! You’d have to somehow learn the correct public key of the target server to be able to match it to the fingerprint you are being shown.
I don’t know how well that will work.
The good news for me personally is that I’m not behind these kind of firewalls in my regular networks – although I don’t honestly know what my Internet service providers are using. They could be doing these kind of things.
I don’t consider this a good thing that firewalls are now doing this. We need to trust the security of services like SSH. This decreases overall trust.
Photo credit: El Taller del Bit on Flickr